“Nice New Pipeline You’ve Got There. Shame If Something Happened to It.”
Covert Actions, Mysteries, Nord Stream Pipelines

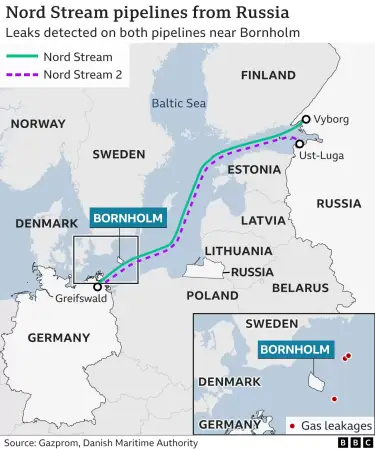
Nord Stream Pipeline leaking into the Baltic Sea.
CNBC:
Nord Stream AG, the operator of the two pipelines, said Tuesday that three known gas leaks caused “unprecedented” damage. The company added that it was not possible to determine when the gas network system’s capacity would be restored.
Seismologists on Monday reported explosions in the vicinity of the unusual Nord Stream gas leaks, prompting gas to spew into the Baltic Sea.
Denmark’s armed forces said video footage showed the largest gas leak created a surface disturbance of roughly 1 kilometer (0.62 miles) in diameter, while the smallest leak caused a circle of approximately 200 meters.
Danish and Swedish authorities declared a no-shipping zone around the location of the leak, which is situated in international waters but inside Denmark and Sweden’s exclusive economic zone.
The cause is not yet known. Some European leaders have suggested possible sabotage, particularly as the suspected attack comes amid a bitter energy standoff between Brussels and Moscow.
—————————
BBC:
Ukraine has accused Russia of causing leaks in two major gas pipelines to Europe in what it described as a “terrorist attack”.
Ukrainian presidential adviser Mykhaylo Podolyak said the damage to Nord Stream 1 and 2 was “an act of aggression” towards the EU.
He added that Russia wanted to cause pre-winter panic and urged the EU to increase military support for Ukraine.
Seismologists reported underwater blasts before the leaks emerged.
“There is no doubt that these were explosions,” said Bjorn Lund of Sweden’s National Seismology Centre, as quoted by local media.
The operators of Nord Stream 2 warned of a loss of pressure in the pipeline on Monday afternoon. That led to a warning from Danish authorities that ships should avoid the area near the island of Bornholm.
The operator of Nord Stream 1 said the undersea lines had simultaneously sustained “unprecedented” damage in one day.
Denmark’s Defence Command has released footage of the leaks which shows bubbles at the surface of the Baltic Sea near the island.
The largest patch of sea disturbance is 1km (0.6 miles) in diameter, it says.
“Gas leak from NS-1 [Nord Stream 1] is nothing more than a terrorist attack planned by Russia and an act of aggression towards the EU. Russia wants to destabilise the economic situation in Europe and cause pre-winter panic,” Ukraine’s Mr Podolyak tweeted in English.
He also called on European partners, particularly Germany, to increase military support for Ukraine.
“The best response and security investment are tanks for Ukraine. Especially German ones,” he said.
Other European leaders have raised the idea that the damage to the pipelines was deliberately inflicted.
Polish Prime Minister Mateusz Morawiecki blamed it on sabotage and said it was probably linked to the war in Ukraine.
Denmark’s Prime Minister, Mette Frederiksen, said it was too early to come to conclusions, but that it was hard to imagine the multiple leaks could be a coincidence.
At the same time, unconfirmed reports in German media said authorities were not ruling out an attack on the undersea gas network.
A Kremlin spokesperson, Dmitry Peskov, said he was “extremely concerned” about the incident, and the possibility of a deliberate attack could not be ruled out.
The EU has previously accused Russia of using a reduction in gas supplies as an economic weapon, in response to European sanctions imposed because of Russia’s invasion of Ukraine.
However, Moscow denies this, saying the sanctions have made it impossible to maintain the gas infrastructure properly.
—————————
Thank you, USA. pic.twitter.com/nALlYQ1Crb
— Radek Sikorski MEP (@radeksikorski) September 27, 2022
Eugyppius suspects that we did it.
Radosław Sikorski, MEP, former Polish defence minister and husband of well-connected neoconservative intellectual Anne Appelbaum, has publicly thanked the United States for attacking the Nord Stream pipelines. (see above)
Jim Geraghty, senior political correspondent for the American political journal National Review, has also praised the attacks in a brief column under the headline “Who Will Rid Me of This Meddlesome Pipeline?” He’s been arguing about the importance of taking Nord Stream 2 offline since February, and suggests that the present attacks reflect his influence.
The biggest detail to break since I went to sleep yesterday, is this claim made by an anonymous intelligence source to Der Spiegel, that the CIA had warned Germany of Baltic pipeline attacks over the summer.
Snowden and China
China, Covert Actions, Edward Snowden, Espionage
Gordon Chang notes the numerous details pointing to Snowden operating in collaboration with China.
By that time, there was no point for China to give Snowden a Beijing palace where he could pet phoenixes.
“Ask yourself: if I were a Chinese spy, why wouldn’t I have flown directly into Beijing? I could be living in a palace petting a phoenix by now.” So wrote Edward Snowden in the middle of last month, in a live chat with readers of London’s Guardian.
Today, the famous 30-year-old cuts a pathetic figure, presumably still marooned in the transit zone in Moscow’s Sheremetyevo International Airport. He has, we are told, remained there since June 23, when he arrived, without passport or Russian visa, on an Aeroflot flight from Hong Kong. Snowden, through the assistance of the WikiLeaks organization, has filed a reported 27 requests for asylum. Venezuela’s president, Nicolas Maduro, offered him refuge on Friday, and Bolivian leader Evo Morales followed suit on Saturday, but China has yet to welcome him.
Beijing’s refusal to accept Snowden suggests he is not a Chinese agent, at least if we accept the premise of his argument outlined for the readers of the Guardian. Nonetheless, there are aspects of his relationship with the People’s Republic of China that are, at the very least, unsettling.
As an initial matter, China may have helped him gather information from the National Security Agency. Sources in the American intelligence community suspect the famous “leaker” was really a “drop box,” receiving information from others in NSA who were working for China. It was his job to act as the courier.
This theory explains how Snowden could possess information to which he did not have access. It is possible he figured out how to bypass barriers in NSA’s systems, but it is more likely he had help. Eli Lake of the Daily Beast reports that the FBI is investigating whether Snowden obtained documents “from a leak inside the secret FISA court.” Similarly, Mike Rogers, chairman of the House Select Committee on Intelligence, has suggested Snowden probably had an accomplice in the NSA who gave him information.
Beijing may also have encouraged Mr. Snowden to leave Hawaii. One of my sources indicates that Chinese intelligence, either directly or through FBI personnel working for China, tipped Snowden off that NSA investigators were closing in on him.
There still is no proof of this allegation, but it is telling that Snowden chose to run to Hong Kong. At first glance, that city is a curious choice for someone trying to avoid American justice. It has the equivalent of an extradition agreement with the U.S. — as a non-sovereign it technically “surrenders” suspects, not extradites them — and a well-known history of close cooperation with American law enforcement. The Guardian, referring to Snowden, stated that “he believed that it was one of the few places in the world that both could and would resist the dictates of the U.S. government.” In view of Hong Kong’s record of regularly turning over suspects to America, this had to mean Snowden thought Beijing would step in to protect him.
Why would he ever think that? It seems clear that Snowden, if he did not actually work for the Chinese, at least did their bidding. He insisted, for instance, that the Washington Post time its initial disclosures so that they would occur on the eve of last month’s “shirtsleeves” summit between President Obama and his Chinese counterpart, Xi Jinping. When the Post refused to give a guarantee — we learned this from Wolf Blitzer’s June 10 interview with the paper’s Barton Gellman — Snowden dealt mostly with the Guardian, which evidently proved to be more pliable. The timing of the Guardian’s disclosures benefited the Chinese enormously, changing the global narrative from Chinese hacking to American surveillance. …
The Chinese then did their best to make sure that American officials did not get the opportunity to interrogate Snowden. The last thing they wanted was for the U.S. to have the opportunity to learn the extent of China’s penetration of the NSA and the FBI in Hawaii. Therefore, they ensured he left Hong Kong before the city could “surrender” him. Albert Ho, one of Snowden’s attorneys, has publicly stated that Beijing approached him through intermediaries who said his client should leave Hong Kong. And as we know by now, this is exactly what Snowden did.
By that time, there was no point for China to give him a Beijing palace where he could pet phoenixes. Ministry of State Security agents had been in contact with Snowden while he was in Hong Kong and probably obtained all they wanted from his four laptops and one thumb drive. Bill Gertz of the Washington Free Beacon reports that U.S. officials say Russian and Chinese intelligence operatives obtained access to, in the words of Gertz, “highly classified U.S. intelligence and military information contained on electronic media” held by Snowden.
At this moment, we do not know whether Snowden, during his time in Hong Kong, actually traveled to China, as some believe, and we do not know the extent of his dealings with the Chinese. Yet the information we do possess — and the suppositions we can reasonably make — point to troubling conclusions.
Read the whole thing.
A Joke
Arthur Conan Doyle, Covert Actions, Humor
As a joke, Arthur Conan Doyle once sent five letters to five friends that read, “We are discovered, flee immediatelyâ€, to see what they would do. One of them disappeared and Conan Doyle never saw him again.
it’s worth mentioning that those friends were people in high places in the government.
Via Madame Scherzo.
This Administration Wouldn’t Lie to Us, Would It?
Covert Actions, DEBKAFile, Hillary Clinton, Iran, Job W. Price, Rumors

Secretary of State Hillary Rodham Clinton
Mossad-mouthpiece DEBKAfile describes the timeline of Hillary Clinton’s mysterious illness:
[Secretary of State Hillary Clinton] cancelled without notice, her participation in the Friends of Syria forum in Marrakesh on Dec, 6. Not only was she one of the founders of this forum, but her presence was vitally needed at the time because NATO and Washington were picking up suspicious movements of the Syrian army’s chemical weapons, which marked a disastrous turn in the Syrian conflict.
She was first reported to have come down with flu and, three days later, on Dec, 9, with a stomach bug.
On Dec. 10, the day before she was due to testify before the Senate Intelligence Committee on the September 11 terrorist attack on the US Consulate in Benghazi – in which Ambassador Chris Stevens and three other US diplomats lost there lives – the State Department which has been heavily under fire over the episode, announced that Clinton had sustained a concussion after fainting out from dehydration.
None of the details normally released in such cases, such as when exactly she fainted, the seriousness of the concussion she suffered or how she was being treated, was offered. A State Department source was only willing to say it was “not severe.†…
[On] Friday, Dec. 21, President Barack Obama announced the nomination of Massachusetts Senator John Kerry as next Secretary of State. Clinton had made it known for some time that she intended stepping down at the start of Obama’s second term of office. … Nothing was said on this occasion about her state of health.
But around Tehran and the Gulf Emirates, debkafile was already picking up insistent rumors claiming that Clinton was seriously injured while on a secret mission in the region in the first week of December. Some claimed that in the same incident, Americans in her party – advisers and security personnel – were either injured or killed. Those rumors did not say what her secret mission was. However, the episode described occurred shortly after Dec. 1, when, as debkafile reported at the time, Obama administration officials and senior representatives of Ayatollah Ali Khamenei launched secret talks on Iran’s nuclear program.
———————
On December 23: USAToday reported:
U.S. military officials are investigating the apparent suicide of a Navy SEAL commander in Afghanistan.
Navy SEAL Cdr. Job W. Price, 42, of Pottstown, Pa., died Saturday of a non-combat-related injury while supporting stability operations in Uruzgan Province, Afghanistan.
———————
A new Foreign Military Intelligence (GRU) report circulating in the Kremlin today is saying that United States Secretary of State Hillary Clinton was injured, and a top US Navy Seal Commander killed when their C-12 Huron military passenger and transport aircraft crash landed nearly 3 weeks ago in the Iranian city of Ahvaz near the Iraqi border.
Iranian intelligence agents quoted in this GRU report confirm that the C-12 Huron aircraft is still in their possession in Ahvaz, but will only admit that the plane was “forced to land because of technical problemsâ€.
The US Navy Seal member reported killed in this bizarre incident, this report says, was indentified as Commander Job W. Price [photo 3rd right] who as a leader of this highly specialized American Special Forces unit protects high-ranking diplomats traveling in Middle Eastern and Asian combat zones. …
Th[e] GRU report, however, states that US military flight logs recorded by Russian air and space forces confirm that Commander Price, and other members of US Navy Seal Team 4, left their base in Urozgan Province, Afghanistan on a flight to US Naval Support Activity Bahrain where they met up with Secretary Clinton and all of them transferred to the C-12 Huron that began a flight path to Baghdad, Iraq.
Within minutes of leaving Bahrain airspace, this report says, the C-12 Huron carrying Secretary Clinton and her US Navy Seal protectors, “without notice,†deviated from their assigned flight path heading, instead, directly towards Iran’s Ahwaz International Airport where, coincidentally, Iranian President Mahmoud Ahmadinejad had previously landed on an “unscheduled†visit. …
Upon the C-12 Huron landing at Ahwaz, however, this report says it encountered “extreme turbulence†causing it to leave the runway where its main landing gear then collapsed causing it to crash.
Within seconds of the C-12 Huron crashing, this report continues, Iranian emergency and security personal responded freeing the victims, including Secretary Clinton who was reportedly unconscious and “bleeding profusely.â€
After emergency aid was given, GRU agents stationed in Iran state that another US military flight was dispatched from Bahrain to Ahwaz which evacuated all of those wounded and killed in the crash including Secretary Clinton.
Strangely to note, this report says, is that in the aftermath of this crash, Iran’s main oil company announced today that they were buying the Ahwaz airport with the intention of moving it because, they say, oil was discovered beneath it.
“Dishonorable Disclosures”
2012 Election, Barack Obama, Covert Actions, Intelligence, Leaks, Obama Administration, Political Ads
In this political ad, a variety of retired military and intelligence officers and special forces operatives go after Barack Obama and the Obama Administration for leaking sensitive national security information for political gain.
Bigger Than Stuxnet
Covert Actions, Flame, Iran, Middle East, Software
The Russian cybersecurity company Kaspersky has discovered that a truly massive piece of malware has been lurking on computers in Iran and other Islamic locations for at least two years. The software discovered is believed to be state-sponsored, and everyone is refraining in print from finger-pointing at the United States.
A massive, highly sophisticated piece of malware has been newly found infecting systems in Iran and elsewhere and is believed to be part of a well-coordinated, ongoing, state-run cyberespionage operation.
The malware, discovered by Russia-based anti-virus firm Kaspersky Lab, is an espionage toolkit that has been infecting targeted systems in Iran, Lebanon, Syria, Sudan, the Israeli Occupied Territories and other countries in the Middle East and North Africa for at least two years.
Dubbed “Flame†by Kaspersky, the malicious code dwarfs Stuxnet in size – the groundbreaking infrastructure-sabotaging malware that is believed to have wreaked havoc on Iran’s nuclear program in 2009 and 2010. Although Flame has both a different purpose and composition than Stuxnet, and appears to have been written by different programmers, its complexity, the geographic scope of its infections and its behavior indicate strongly that a nation-state is behind Flame, rather than common cyber-criminals — marking it as yet another tool in the growing arsenal of cyberweaponry.
The researchers say that Flame may be part of a parallel project created by contractors who were hired by the same nation-state team that was behind Stuxnet and its sister malware, DuQu.
“Stuxnet and Duqu belonged to a single chain of attacks, which raised cyberwar-related concerns worldwide,†said Eugene Kaspersky, CEO and co-founder of Kaspersky Lab, in a statement. “The Flame malware looks to be another phase in this war, and it’s important to understand that such cyber weapons can easily be used against any country.â€
Early analysis of Flame by the Lab indicates that it’s designed primarily to spy on the users of infected computers and steal data from them, including documents, recorded conversations and keystrokes. It also opens a backdoor to infected systems to allow the attackers to tweak the toolkit and add new functionality.
The malware, which is 20 megabytes when all of its modules are installed, contains multiple libraries, SQLite3 databases, various levels of encryption — some strong, some weak — and 20 plug-ins that can be swapped in and out to provide various functionality for the attackers. It even contains some code that is written in the LUA programming language — an uncommon choice for malware.
Kaspersky Lab is calling it “one of the most complex threats ever discovered.â€
“It’s pretty fantastic and incredible in complexity,†said Alexander Gostev, chief security expert at Kaspersky Lab.
Flame appears to have been operating in the wild as early as March 2010, though it remained undetected by antivirus companies.
“It’s a very big chunk of code. Because of that, it’s quite interesting that it stayed undetected for at least two years,†Gostev said. He noted that there are clues that the malware may actually date back to as early as 2007, around the same time-period when Stuxnet and DuQu are believed to have been created.
Read the whole thing.
Inside Story Worse Than the Rumors
CIA, Covert Actions, John O. Brennan, Leaks, MI6, Obama Administration, Yemen

John O. Brennan, Deputy National Security Advisor for Homeland Security and Counterterrorism, and Assistant to the President
Michael A. Walsh, in the New York Post, spills the beans on the damaging leak which has seriously compromised relations between British and American intelligence services.
So that “CIA coup†in Yemen against another al Qaeda underwear bomber turns out to actually have been a joint Saudi-British intelligence operation — which apparently was prematurely terminated thanks to flapping lips on this side of the Atlantic.
So the leak didn’t just blow our chances to nail the notorious bomb designer behind the plot, Ibrahim al-Asiri, and put the life of the double agent in mortal danger for no reason.
It also seriously damaged Langley’s relationship with its foreign counterparts, who now understand that operational security and the lives of their operatives mean nothing to us (not in an election year, anyway).
Which makes it even more important to find out: Who leaked?
The betting starts with former CIA official John Brennan, the White House’s deputy nationalsecurity adviser for counterterrorism. Shortly after details about the operation leaked to the Associated Press via unnamed “officials,†Brennan took to the airwaves to crow publicly about how the wedgie bomber was “no longer a threat to the American people.â€
And the AP admitted it cleared its story with the feds in advance.
The uncharitable immediately saw this naked self-aggrandizement as a blatant attempt by the Obama administration to take political credit for something it had almost nothing to do with.
Read the whole thing.
Someone in Langley Underestimated Tehran’s Capabilities
Covert Actions, Intelligence, Iran, Sentinel Drone

Iranians gloat over US RQ-170 Sentinel drone downed last week
The Christian Science Monitor has an exclusive story which must be causing some serious embarrassment in parts of the US military and intelligence community.
Iran guided the CIA’s “lost” stealth drone to an intact landing inside hostile territory by exploiting a navigational weakness long-known to the US military, according to an Iranian engineer now working on the captured drone’s systems inside Iran.
Iranian electronic warfare specialists were able to cut off communications links of the American bat-wing RQ-170 Sentinel, says the engineer, who works for one of many Iranian military and civilian teams currently trying to unravel the drone’s stealth and intelligence secrets, and who could not be named for his safety.
Using knowledge gleaned from previous downed American drones and a technique proudly claimed by Iranian commanders in September, the Iranian specialists then reconfigured the drone’s GPS coordinates to make it land in Iran at what the drone thought was its actual home base in Afghanistan.
“The GPS navigation is the weakest point,” the Iranian engineer told the Monitor, giving the most detailed description yet published of Iran’s “electronic ambush” of the highly classified US drone. “By putting noise [jamming] on the communications, you force the bird into autopilot. This is where the bird loses its brain.”
The “spoofing†technique that the Iranians used – which took into account precise landing altitudes, as well as latitudinal and longitudinal data – made the drone “land on its own where we wanted it to, without having to crack the remote-control signals and communications†from the US control center, says the engineer.In 2009, Iran-backed Shiite militants in Iraq were found to have downloaded live, unencrypted video streams from American Predator drones with inexpensive, off-the-shelf software. But Iran’s apparent ability now to actually take control of a drone is far more significant.
Iran asserted its ability to do this in September, as pressure mounted over its nuclear program.
Gen. Moharam Gholizadeh, the deputy for electronic warfare at the air defense headquarters of the Islamic Revolutionary Guard Corps (IRGC), described to Fars News how Iran could alter the path of a GPS-guided missile – a tactic more easily applied to a slower-moving drone.
“We have a project on hand that is one step ahead of jamming, meaning ‘deception’ of the aggressive systems,†said Gholizadeh, such that “we can define our own desired information for it so the path of the missile would change to our desired destination.â€
Gholizadeh said that “all the movements of these [enemy drones]†were being watched, and “obstructing†their work was “always on our agenda.â€
That interview has since been pulled from Fars’ Persian-language website. And last month, the relatively young Gholizadeh died of a heart attack, which some Iranian news sites called suspicious – suggesting the electronic warfare expert may have been a casualty in the covert war against Iran. …
Secretary of Defense Leon Panetta told Fox News on Dec. 13 that the US will “absolutely” continue the drone campaign over Iran, looking for evidence of any nuclear weapons work. But the stakes are higher for such surveillance, now that Iran can apparently disrupt the work of US drones.
US officials skeptical of Iran’s capabilities blame a malfunction, but so far can’t explain how Iran acquired the drone intact. One American analyst ridiculed Iran’s capability, telling Defense News that the loss was “like dropping a Ferrari into an ox-cart technology culture.â€
Yet Iran’s claims to the contrary resonate more in light of new details about how it brought down the drone – and other markers that signal growing electronic expertise.
A former senior Iranian official who asked not to be named said: “There are a lot of human resources in Iran…. Iran is not like Pakistan.”
US Air Force Drones Virused
Covert Actions, Drones, Hacking, US Air Force, Virus
Noah Schachtman, at Wired’s Danger Room, broke the news of an extraordinary electronic warfare coup by an unnamed foreign adversary.
A computer virus has infected the cockpits of America’s Predator and Reaper drones, logging pilots’ every keystroke as they remotely fly missions over Afghanistan and other warzones.
The virus, first detected nearly two weeks ago by the military’s Host-Based Security System, has not prevented pilots at Creech Air Force Base in Nevada from flying their missions overseas. Nor have there been any confirmed incidents of classified information being lost or sent to an outside source. But the virus has resisted multiple efforts to remove it from Creech’s computers, network security specialists say. And the infection underscores the ongoing security risks in what has become the U.S. military’s most important weapons system.
“We keep wiping it off, and it keeps coming back,†says a source familiar with the network infection, one of three that told Danger Room about the virus. “We think it’s benign. But we just don’t know.â€
Military network security specialists aren’t sure whether the virus and its so-called “keylogger†payload were introduced intentionally or by accident; it may be a common piece of malware that just happened to make its way into these sensitive networks. The specialists don’t know exactly how far the virus has spread. But they’re sure that the infection has hit both classified and unclassified machines at Creech. That raises the possibility, at least, that secret data may have been captured by the keylogger, and then transmitted over the public internet to someone outside the military chain of command. …
The GCSs handling more exotic operations are top secret. None of the remote cockpits are supposed to be connected to the public internet. Which means they are supposed to be largely immune to viruses and other network security threats.
But time and time again, the so-called “air gaps†between classified and public networks have been bridged, largely through the use of discs and removable drives. In late 2008, for example, the drives helped introduce the agent.btz worm to hundreds of thousands of Defense Department computers. The Pentagon is still disinfecting machines, three years later.
Use of the drives is now severely restricted throughout the military. But the base at Creech was one of the exceptions, until the virus hit. Predator and Reaper crews use removable hard drives to load map updates and transport mission videos from one computer to another. The virus is believed to have spread through these removable drives. Drone units at other Air Force bases worldwide have now been ordered to stop their use.
In the meantime, technicians at Creech are trying to get the virus off the GCS machines. It has not been easy. At first, they followed removal instructions posted on the website of the Kaspersky security firm. “But the virus kept coming back,†a source familiar with the infection says. Eventually, the technicians had to use a software tool called BCWipe to completely erase the GCS’ internal hard drives. “That meant rebuilding them from scratch†— a time-consuming effort.
The Air Force declined to comment directly on the virus. “We generally do not discuss specific vulnerabilities, threats, or responses to our computer networks, since that helps people looking to exploit or attack our systems to refine their approach,†says Lt. Col. Tadd Sholtis, a spokesman for Air Combat Command, which oversees the drones and all other Air Force tactical aircraft.
Reports I’ve read quoting the Wired ask the silly question: was the infection accidental or deliberate. No one else has mentioned the obvious suspect: China. The good news is that the infection is apparently confined specifically to Creech.
Major Cyberattack Revealed
China, Covert Actions, Hackers, Hacking, Technology
An IBD editorial mentions the kind of news items that won’t be making the New York Times’ front page: Chinese steal thousands of secret documents from defense contractor’s computers, and a member of the US Joint Chiefs of Staff announces that the US intends to develop methods of retaliation for such attacks.
In outlining America’s cyberwarfare strategy last Thursday at the National Defense University, Deputy Secretary of Defense William Lynn disclosed that 24,000 sensitive files containing Pentagon data at a defense company were accessed in a cyberattack in March, likely by a foreign government.
He didn’t disclose the identity of that government, but in a bit of an understatement he acknowledged, “We have a pretty good idea.” So do we: the People’s Republic of China. In addition to conventional and nuclear weaponry, China has invested a great deal of time and treasure in what is known as “asymmetrical warfare” — the ability to exploit an enemy’s weakness rather than just try to match it tank for tank. …
Marine Gen. James Cartwright, vice chairman of the Joint Chiefs of Staff, said the Pentagon must shift its thinking on cybersecurity from focusing 90% of its energy on building a better firewall. “If your approach to the business is purely defensive in nature, that’s the Maginot line approach,” he said.
He was referring to the French fixed defensive fortifications that were circumvented by the Nazis at the outset of World War II. “There is no penalty for attacking (the U.S.) right now,” he added. We need the ability to retaliate and the will to do so. Call it mutual assured hacking after the deterrence doctrine of mutual assured destruction (MAD) during the Cold War.